Beware of juice jacking: Protect your devices
The attack aims to either infect the device with malware or secretly copy potentially sensitive data
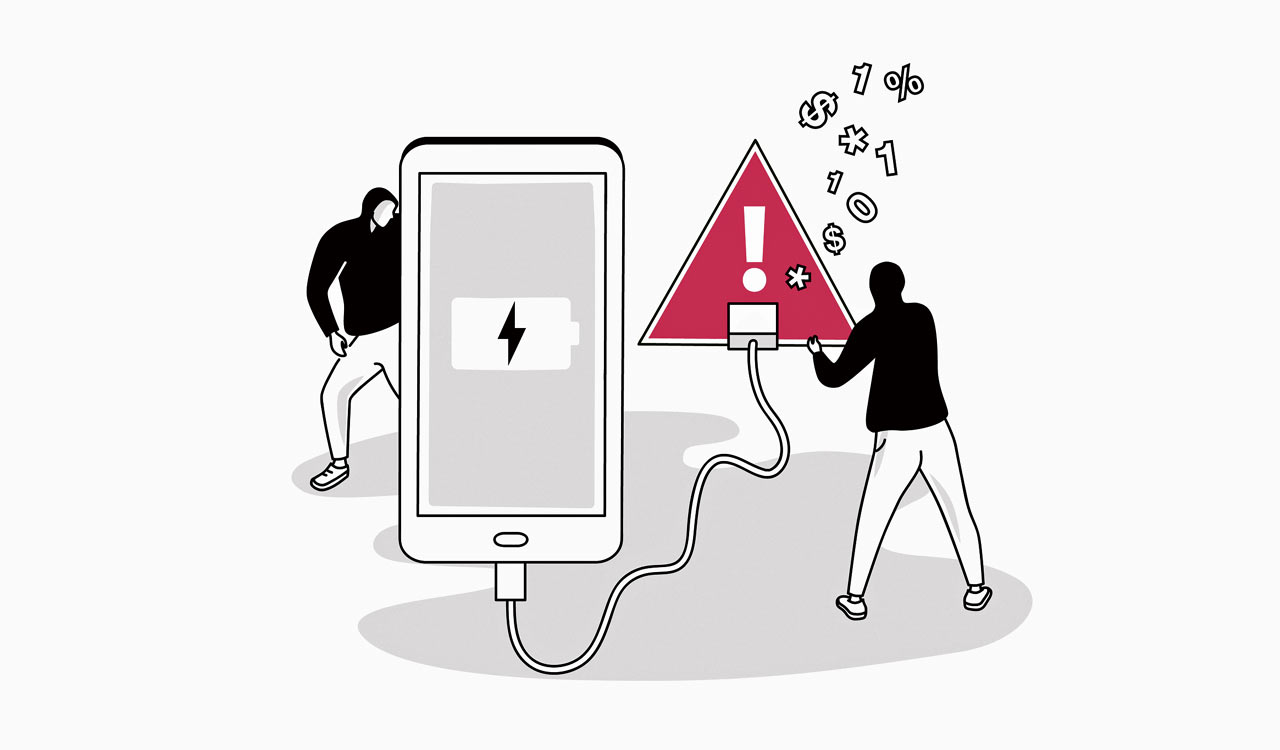
Hyderabad: Devices like smartphones and tablets sharing a USB cable for charging and data transfer may be vulnerable to “juice jacking.” The attack aims to either infect the device with malware or secretly copy potentially sensitive data
What is juice jacking?
A cyberattack known as “juice jacking” occurs when hackers utilise public charging stations, such as coffee shops or airports, to install malware or steal data from devices. A man-in-the-middle assault with a hardware focus is juice jacking. Malicious software can gain access to your device by connecting your phone or tablet to these vulnerable USB ports, which could result in data theft or unauthorised control.
Operation of juice jacking
-The attacker either infects a connection cable and leaves it plugged in, anticipating that someone will use the “forgotten” wire, or they utilise a USB connection to inject malware directly into the charging station.
– The most often used devices in juice jacking attacks are USB ports and phone charging cords. Other uncommon gadgets can be portable battery power banks and video arcade machines with USB connectors.
-Because data is transferred via the same connector that charges a device, juice jacking weaknesses are effective.
Five pins are found on a USB connector. However, only two of the five pins are required for data transfer, and only one is required to charge a connected device. An end user can transfer files between a PC and a mobile device while the latter is plugged into a charging station
Avoid being the victim
– Rather than using a USB charging station, connect your smartphone to a standard wall socket if one is available.
– Keep your charger with you, bring a USB data blocker that permits electricity to flow through but prevents data transfer, or a portable charger.
– Disable data transfer to stop data access while connected to unknown USB ports, and turn your device into charge-only mode if it permits.
– Be cautious about where and how you charge your devices in public places.
Related News
-
Cartoon Today on December 25, 2024
3 hours ago -
Sandhya Theatre stampede case: Allu Arjun questioned for 3 hours by Chikkadpallly police
4 hours ago -
Telangana: TRSMA pitches for 15% school fee hike and Right to Fee Collection Act
4 hours ago -
Former Home Secretary Ajay Kumar Bhalla appointed Manipur Governor, Kerala Governor shifted to Bihar
4 hours ago -
Hyderabad: Organs of 74-year-old man donated as part of Jeevandan
4 hours ago -
Opinion: The China factor in India-Nepal relations
4 hours ago -
Editorial: Modi’s Kuwait outreach
4 hours ago -
Telangana HC suspends orders against KCR and Harish Rao
5 hours ago
